Gcore Radar Report Reveals 41% Surge in DDoS Attack Volumes
Luxembourg, Luxembourg, Sept. 25, 2025 (GLOBE NEWSWIRE) -- Gcore, the global edge AI, cloud, network, and security solutions provider, today announced the findings of its Q1-Q2 2025 Radar report into DDoS attack trends. DDoS attacks have reached unprecedented scale and disruption in 2025, and businesses need to act fast to protect themselves from this evolving threat. The report reveals a significant escalation in the total number of DDoS attacks and their magnitude, measured in terabits per second (Tbps).
It also highlights a clear shift: attackers are growing more strategic, blending brute-force volume with precise application-layer manipulation.
Key Insights From Q1-Q2 2025
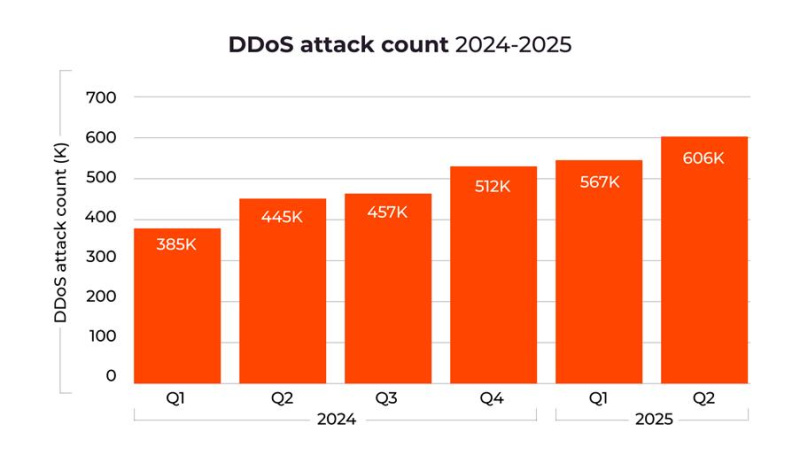
· Attack volumes increased by 41% compared to Q1-Q2 2024, evidencing dangerous long term growth trends predicted in prior Radar reports.
· The largest attack peaked at 2.2 Tbps in Q1-Q2, surpassing the 2 Tbps peak recorded in late 2024.
· DDoS attacks are becoming longer in duration but more harmful.
· Attackers are shifting focus to financial services and tech, with tech overtaking gaming as the most targeted sector.
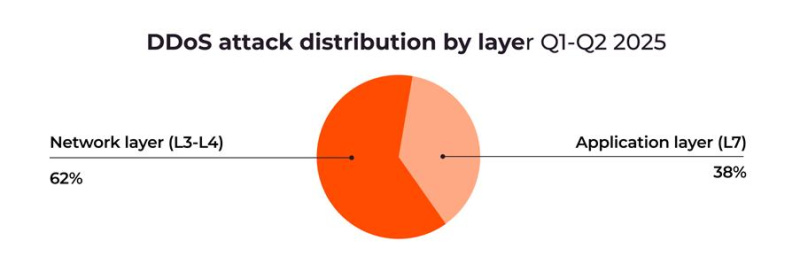
· DDoS attacks at the application layer have increased by 10% from Q3-Q4 2024 to Q1-Q2 2025.
· The total number of DDoS attacks climbed from 969,000 in H2 2024 to 1.17 million in H1 2025.
Andrey Slastenov, Head of Security at Gcore, commented: “The latest Gcore Radar should be a wake-up call to businesses across all industries. Not only are the number and intensity of attacks increasing, but attackers are expanding the scope of their attacks to reach an increasingly wide range of sectors. Businesses must invest in robust DDoS detection, mitigation, and protection to prevent the financial and reputational impact of an attack.’’
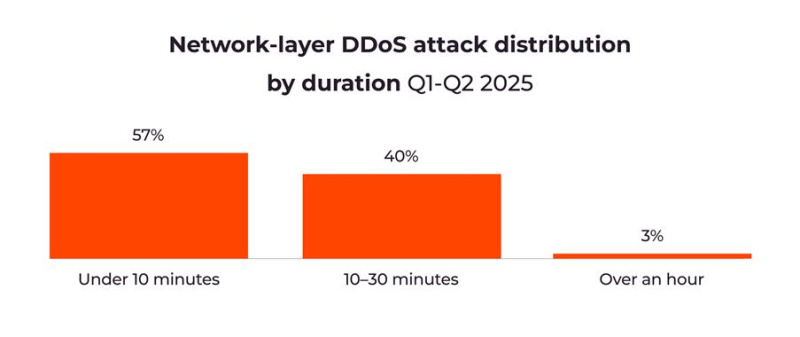
Recent Data Shows Shift Toward Longer Sustained Assaults
Attacks shorter than 10 minutes have decreased by about 33%, while those lasting between 10 and 30 minutes have nearly quadrupled. While previous reports highlighted the dominance of very short, intense DDoS attacks, this change indicates that attackers are adapting to the improved automatic detection and mitigation systems employed by companies to handle brief attacks. By extending attack durations, threat actors can circumvent these temporary defense thresholds, cause more extensive damage, and test infrastructure resilience over time.
Multi-vector attacks have also increasingly become a preferred tactic of attackers. By masking malicious activity within seemingly legitimate traffic, attackers complicate detection and extend their window to cause damage. This shift toward more sophisticated attacks underscores the need for an equally layered defense approach that anticipates attacker strategies and protects critical digital assets holistically.
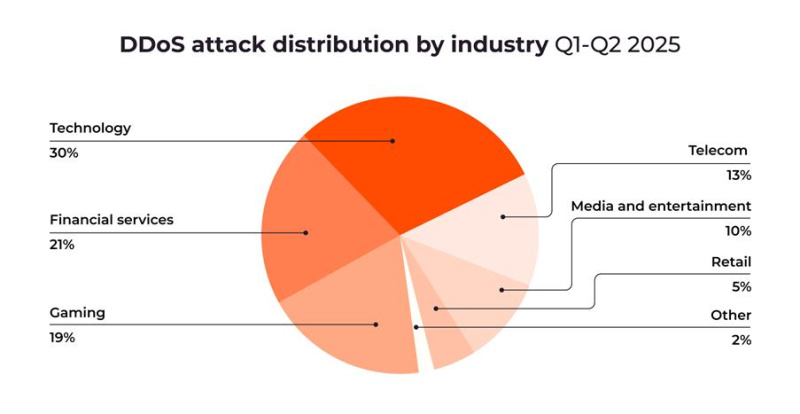
Data Indicates Rise in Attacks on Vulnerable Sectors
Gaming is no longer the dominant target it once was. Its share of total DDoS attacks has dropped significantly (30% in the last year). This notable decline suggests attackers are shifting focus to other sectors such as tech (attacks increased by 15%) and financial services (attacks increased by 15%). These sectors are favored targets because they may be less protected against threat actors and have higher disruption potential.
The Domino Effect of Cyberattacks
Hosting providers, in particular, have become prime targets due to their role supporting SaaS, e-commerce, gaming, and financial clients. An attack on one hosting provider can have dangerous ripple effects: massive service outages and reputation damage to dozens of dependent companies.
Geographical Distribution of DDoS Attacks
With a presence that spans six continents, Gcore can accurately track the geographical sources of DDoS attacks. Gcore derives these insights from the attackers’ IP addresses and the geographic locations of the data centers where malicious traffic is targeted.
Although the United States and the Netherlands remain top sources for attacks (as found in previous Radar reports), Hong Kong is a new source of threats. Hong Kong now accounts for 17% of all network-layer and 10% of application-layer attacks. These findings indicate that attackers are expanding into emerging areas, highlighting the need for proactive and adaptive defenses across diverse regions.
Emerging Origins of Attacks
The rapid increase in application layer attacks (28% to 38% from Q3-Q4 2024 to Q1-Q2 2025) also reveals an overall trend toward multi-layered attacks targeting web application and API vulnerabilities, which particularly impact sectors with a high degree of customer interaction (ranging from e-commerce and online banking to logistics and public services).
To access the full report, please visit: https://gcore.com/resources/gcore-radar-attack-trends-q1-q2-2025
About Gcore
Gcore is a global edge AI, cloud, network, and security solutions provider. Headquartered in Luxembourg, with a team of 600 operating from ten offices worldwide, Gcore provides solutions to global leaders in numerous industries. Gcore manages its global IT infrastructure across six continents, with one of the best network performances in Europe, Africa, and LATAM due to the average response time of 30 ms worldwide. Gcore’s network consists of 210 points of presence worldwide in reliable Tier IV and Tier III data centers, with a total network capacity exceeding 200 Tbps.
Further information is available at gcore.com and updates are also shared on LinkedIn, Twitter, and Facebook.
Gcore Press Contact
pr@gcore.com
PR Agency Contact
gcore@aspectusgroup.com

Contact Ms. Kira Kurepina Gcore kira.kurepina@gcore.com
Legal Disclaimer:
EIN Presswire provides this news content "as is" without warranty of any kind. We do not accept any responsibility or liability for the accuracy, content, images, videos, licenses, completeness, legality, or reliability of the information contained in this article. If you have any complaints or copyright issues related to this article, kindly contact the author above.

